Since the website’s launch, there has not been any documentation or tutorials. As its functionality is relatively simple, little introduction is necessary. However, there are some small details and scenarios that I think would be helpful to share.
Firstly, the website’s basic functionality allows you to query website subdomains, based on IP address or IP range, and it supports IPv6 addresses and address ranges. The current maximum display limit is 10,000 results (which is sufficient for most cases). The query results page also features a CSV export function, allowing you to export all results. Alternatively, you can obtain all results by adding the parameter ?full=1 to your query. Currently, most open-source tools collect data using this method.
Here are two practical scenarios:
Information gathering
When gathering ASN information, you can quickly determine which assets are targeted by querying the reverse IP range.
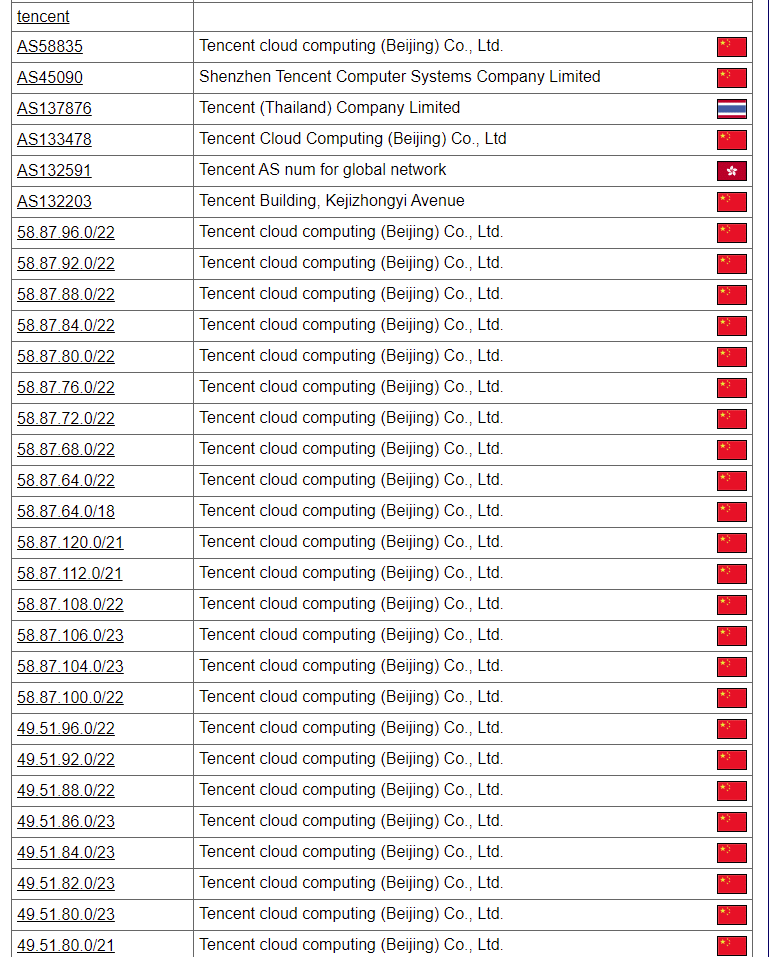
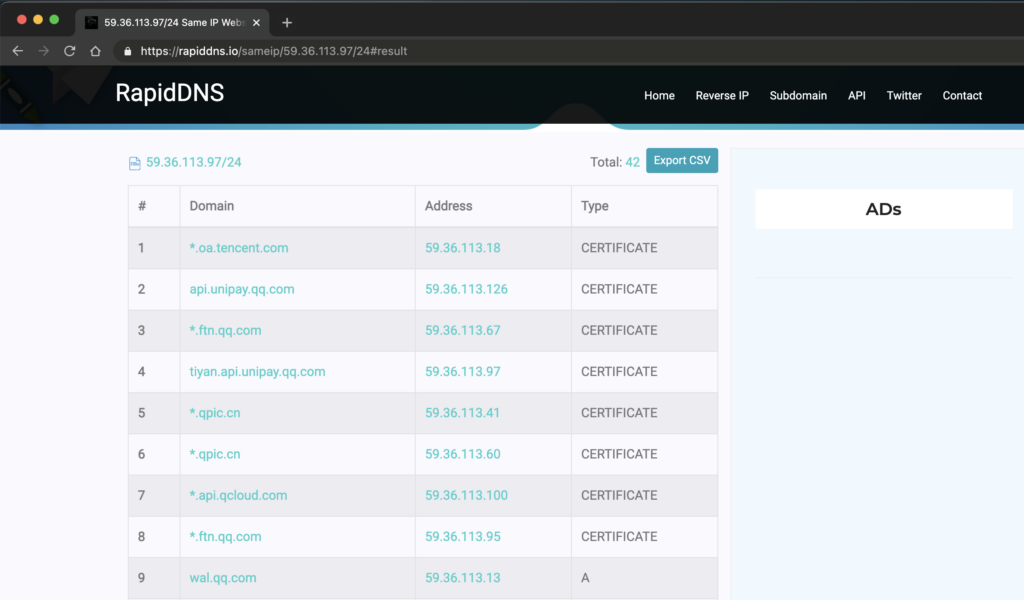
For example, in the search results for Tencent, you will find many IP ranges that belong to Tencent Cloud Services. While these IP ranges may not be particularly useful for exploiting vulnerabilities, they may contain individual targets. You can use the Reverse IP functionality to query and filter out the desired targets or IP ranges.
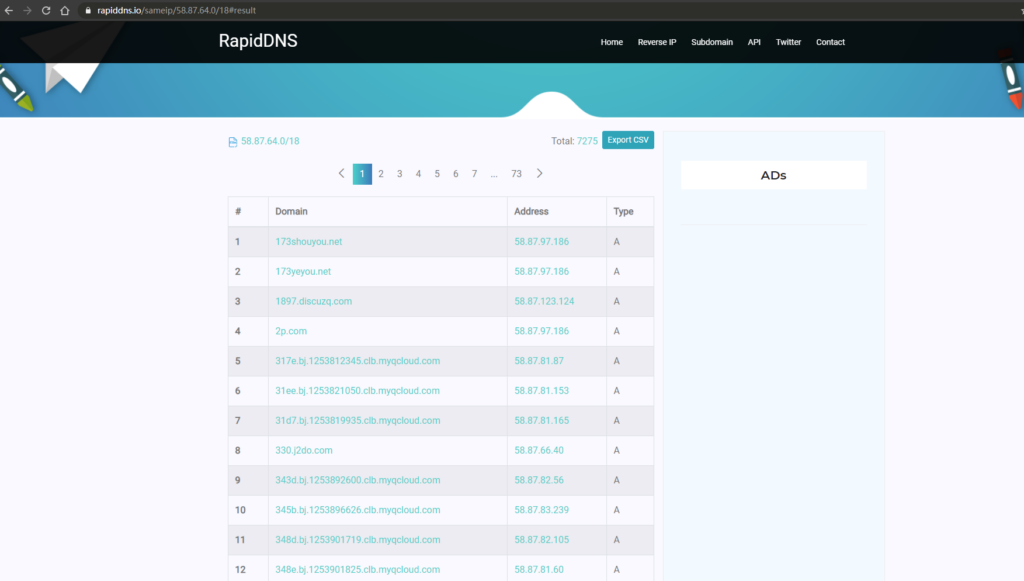
Traceroute
Here are two common scenarios:
- You discover an IP address has a vulnerability and want to know which manufacturer it belongs to.
- You want to determine which organization owns the IP address used in an attack.
There are two common methods for accomplishing these tasks. One method is to directly query the IP address. If the IP address is not found, what can you do?
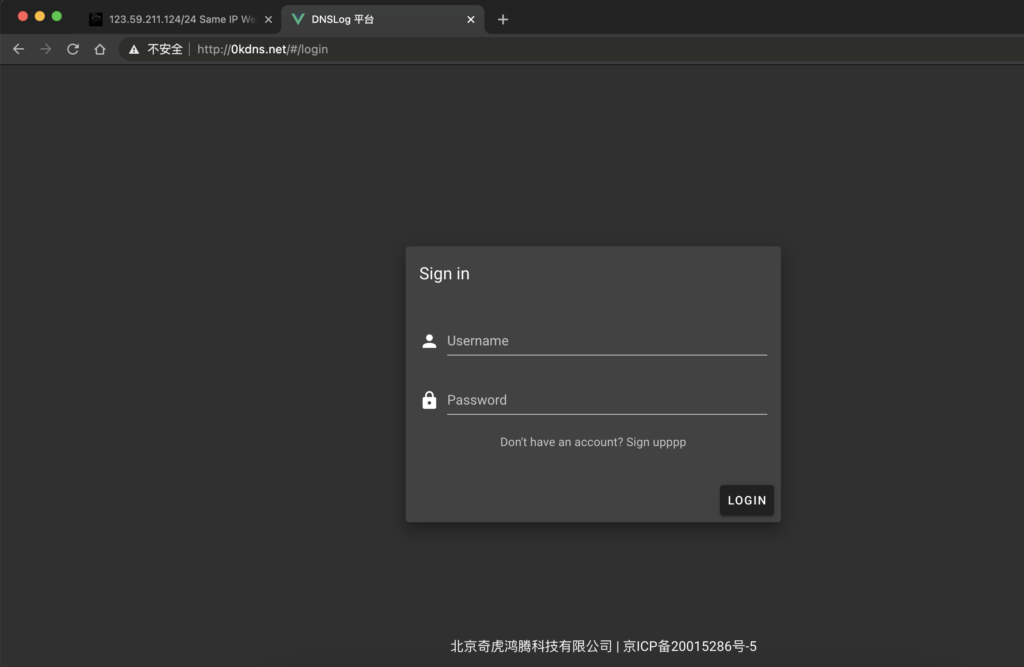
I recently encountered an example in a WeChat group. Someone discovered the address of a dnslog platform belonging to the 360 team in the logs, but the domain name was blank. I was able to quickly find the login address of the dnslog platform by obtaining the resolved IP address and querying the C-block. Based on the copyright information, I confirmed that the platform belonged to 360.
The findings of this investigation were as follows:
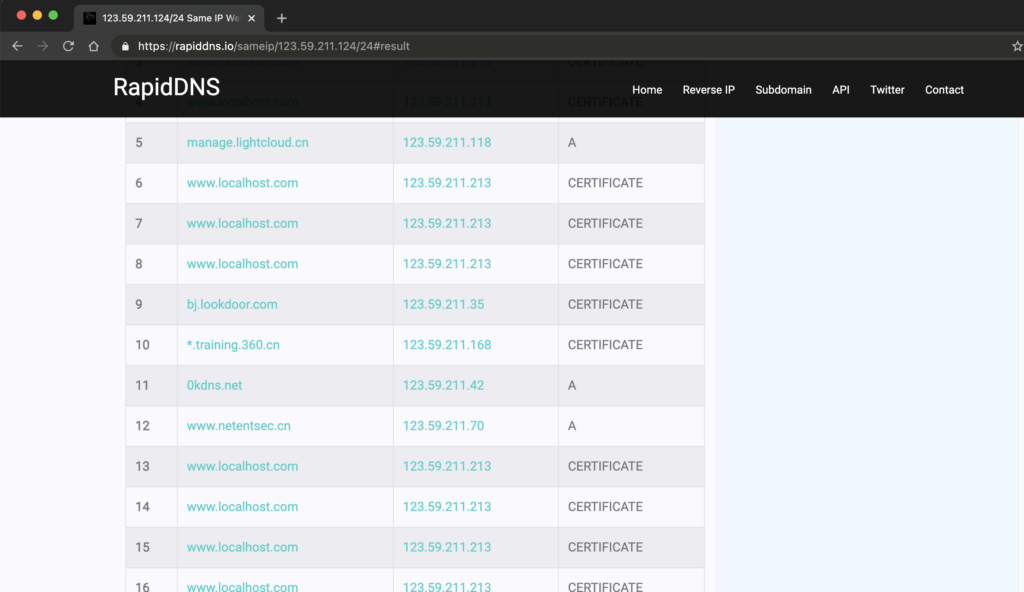
The domain name is 0kdns.net and the login address is dnslog.0kee.360.cn. The resolved IP address is 123.59.211.124. I queried the C-block using RapidDNS and the results showed that the domain name is owned by 0kdns.net.